A Learning Security Organization
When I was six my family spent a year in France as part of a Fulbright exchange. I dragged my parents to every castle I could. I loved to climb around the fortifications and explore the armory museums that were often attached. I recall my father pointing out a particularly imposing suite of full plate armor, with a tiny hole in the left breast plate. This was likely from target practice as I don’t think that armor was ever intended for the field, but the lesson was clear - technology can quickly swing the balance between defense and offense. Complexity and change are dominant factors today - If anything can be relied upon in the modern world it is that nothing can be relied upon for long.
In The Fifth Discipline Peter Senge outlines an organization whose product is learning. He posits that such a ‘learning organization’ is the best model to handle change and complexity, particularly compared with more rigid industrial approaches to knowledge work. Complexity and change are certainly hallmarks of the technology sector, and security, so how could we build a security organization around the principles of learning? Senge’s five disciplines are: Personal Mastery, Mental Models, Shared Vision, Team Learning and Systems Thinking. The first three disciplines are important aspects, but it is the last two where Incident Response can provide the cornerstone of a learning security organization.
The ‘shared vision’ I have tried to develop with my team of how the various security functions work together is represented in the diagram below. This of course reflects my mental models of IR as the driving force in a security program. For me security controls are an output of the enterprise risk management process which is primarily informed by IR and intelligence; whereas many security practitioners think of preventative controls as more central to the program. Which is also a reasonable view.
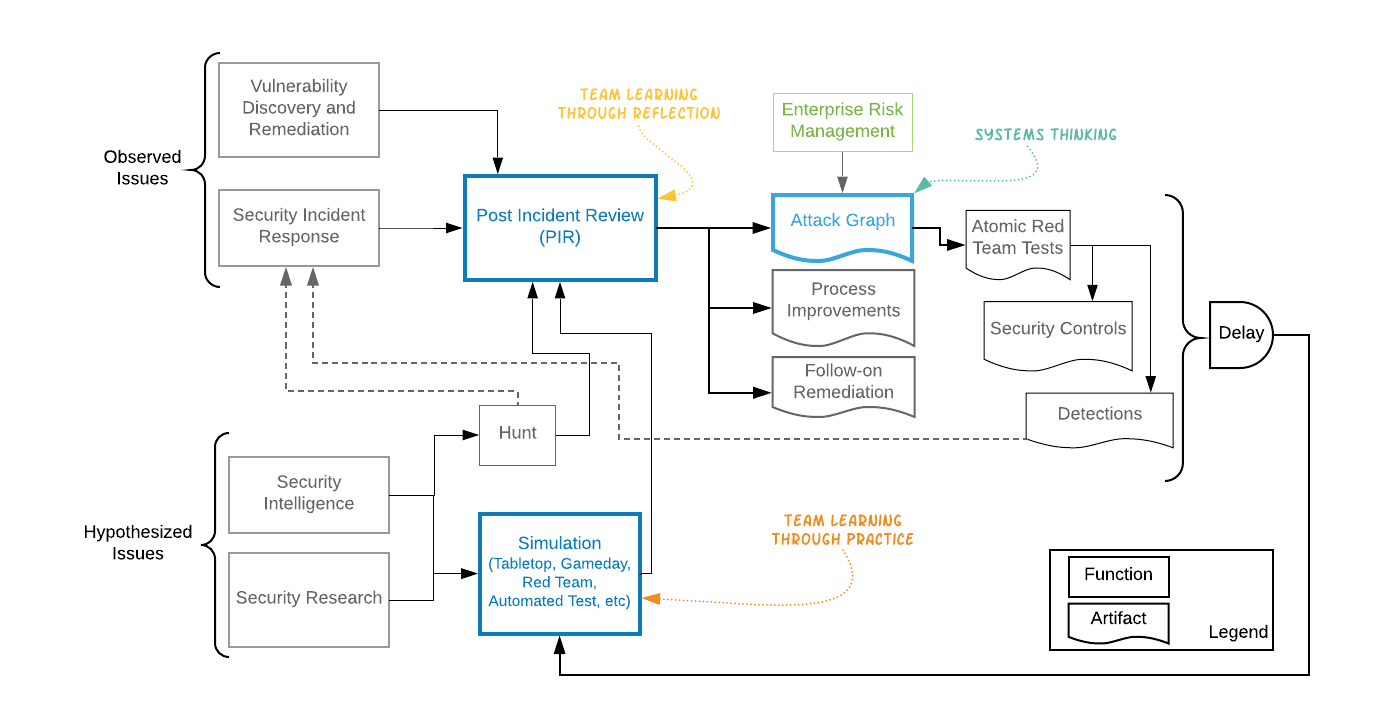
The two areas that IR really shines are in promoting team learning and systems thinking.
Team Learning pulls together the efforts of individuals seeking personal mastery and aligned on a shared vision to improve execution. Systems today are so complex that cross-functional work is a necessity. To get better at working across teams and specialties, you need to learn as a team. Senge suggests team learning is realized through group reflection on past work and practice via group exercises in virtual environments. Thus the two primary engines of team learning are Post Incident Reviews (PIRs) for reflection and Simulations for practice in virtual environments.
Systems Thinking is the titular fifth discipline. To properly diagnose a security problem, one must consider the whole system. To help with this I think the use of attack graphs is compelling. It is easy to fall into local solutions that are globally suboptimal. As has been said ‘attackers think in graphs’ and the attack graph construct encourages both adversarial thinking and provides a framework for considering broader system context. We are experimenting with creating attack graphs as part of our PIR process. Just as you would create a timeline, you also output an attack graph or refine an existing one.
If you follow the flow of the graph from our two engines of learning, Simulations and PIRs, you see that Simulations result in a PIR, and the PIR produces several artifacts. These artifacts are how we inject learning from the IR process back into the overall security organization. The Enterprise Risk Management function provides business context to the technical information derived from IR, and via the attack graphs, drives investments in both preventative controls and detections. We are experimenting with test driven development of our controls, where we first build an attack simulation and then design controls against that. This allows continuous, chaos-style, testing of our security investments for reliability and risk measurement.
In summary, I believe the model of a learning organization is a good fit for security teams. Incident response best practices around PIRs and Simulation are key engines of learning, and attack graphs offer a powerful tool for systems thinking. This post offers several ways to inject that learning back into a security program and highlights attack graphs as an emerging method to promoting systems thinking.